Security Information and Event Management (SIEM)
24 Jul 2021What is SIEM?
While security information and event management (SIEM) solutions have been around for over a decade, and have evolved significantly over that time, the core functionality still acts as the most effective foundation for any organization’s technology stack.
At its most fundamental level, a SIEM solution enables an organization to centrally collect data across its entire network environment to gain real-time visibility into activity that may potentially introduce risk to the organization.
Using SIEM technology to achieve visibility into network activity helps organizations address issues before they become a significant financial risk. It also helps operations better manage company assets.
See a SIEM in Action
LogRhythm can help you tell a cohesive story around user and host data, making it easier to gain proper insight needed to remediate security incidents faster.
In this demo inspired by real-life events, watch a security analyst use our NextGen SIEM Platform to detect a life-threatening cyberattack on a water treatment plant.
How Do SIEM Solutions Work?
The core set of capabilities for a SIEM solution includes data collection, parsing (or normalizing) data, and correlating that data to identify suspicious or problematic activity. This processing and enrichment of data enables all forms of data analysis and can have a direct impact on how effectively an organization can search and access its data.
Once the data has been ingested and normalized, the SIEM software correlates events across all of the data in aggregate to identify patterns of compromise and alert the end user to suspicious activity.
SIEM technology can reside either on-premise (on your own hardware) or in the cloud (on someone else’s hardware) and collect data from a massive variety of data sources.
The SIEM Essentials
- Log Management: Collect, normalize, and aggregate log data to deliver efficient data access and management
- Real-Time Monitoring: Observe activity at the exact moment it occurs within your network environment
- Incident Investigation: Search and drill down on logs to further investigate a potential incident
Benefits of Leveraging SIEM as Your Security/IT Foundation
SIEM solutions map to modern operational needs, delivering real-time visibility, efficient and secure data access, streamlined workflows, a unified user experience, and the ability to customize how you manage your environment based on the demands of the organization.
Some key benefits include:
Value for Security and IT Operations
- Effective collection and normalization of data to enable accurate and reliable analysis
- Real-time visibility across your environment to quickly identify and prioritize potential issues
- Ease of accessing and searching across raw and parsed data for investigation and compliance
- Ability to map your security and IT operations to existing frameworks such as NIST and MITRE ATT&CK
Broad Integration Across Security and IT Vendors
- Support for integration with hundreds of security and IT solutions to further extend SIEM capabilities and data collection
- Central management of all security related solutions that ties together disparate solutions to provide a single pane of glass
Compliance Adherence, Enforcement, and Reporting
- Ensure compliance adherence with real-time visibility and notifications to ensure awareness of all compliance-related activity
- Prebuilt compliance modules automatically detect violations as they occur to remove the burden of manually reviewing audit logs
Learn How LogRhythm Can Help Your Team
Let one of our experts review your use cases and demonstrate how the LogRhythm NextGen SIEM Platform can help you detect and respond to threats faster than ever before.
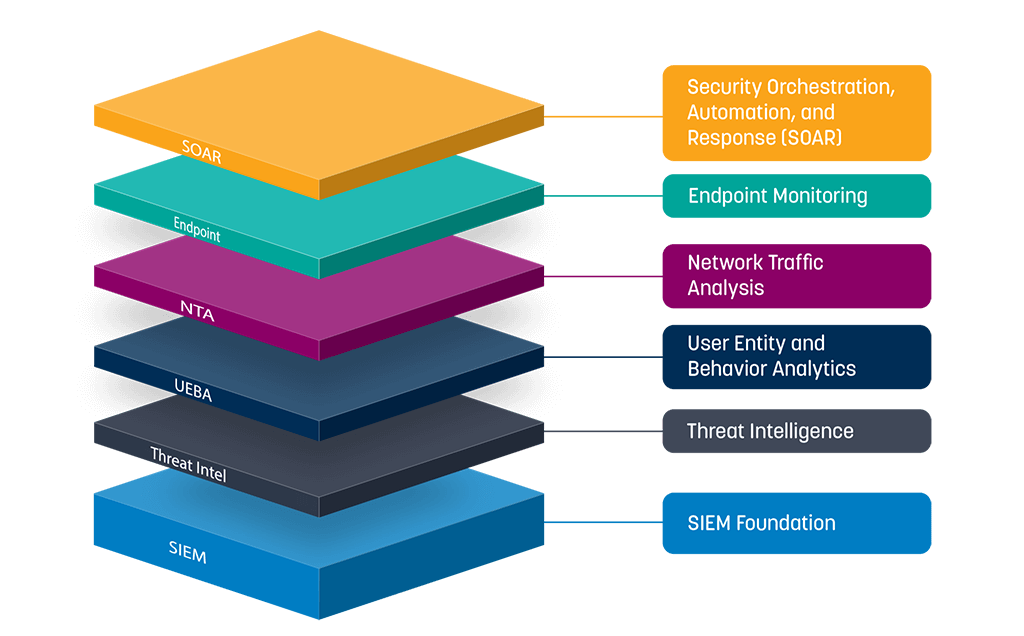
The Evolution of SIEM Software
Learn more: https://logrhythm.com/solutions/security/siem/