Privileged Access Manager
22 Jul 2021Keep your business and its most valuable assets secure. Preventing malicious account or credential access starts with sound privileged access management.

MITIGATE RISKS, MAXIMIZE PRODUCTIVITY
Don’t settle for less than the industry leader in privileged access management (PAM).
Defend Against Attacks
Secure privileged identities – human and machine in a tamper-resistant repository.
Satisfy Audit & Compliance
Meet internal requirements, manage access and maintain full centralized audit.
Enable the Digital Business
Securely authenticate users with VPN-less access from a single web portal.
OUTSMART THE SMARTEST ATTACKERS
Stay one step ahead of cyberattacks. And your competition.

THE BEST DEFENSE IS GOOD CYBERSECURITY
Manage privileged access and minimize risk.
Manage Privileged Credentials
Automatically discover and onboard privileged credentials and secrets used by human and non-human identities. Centralized policy management allows administrators to set policies for password complexity, frequency of password rotations, which users may access which safes, and more. Automated password rotation helps strengthen security while eliminating time-intensive, manual processes for the IT teams.
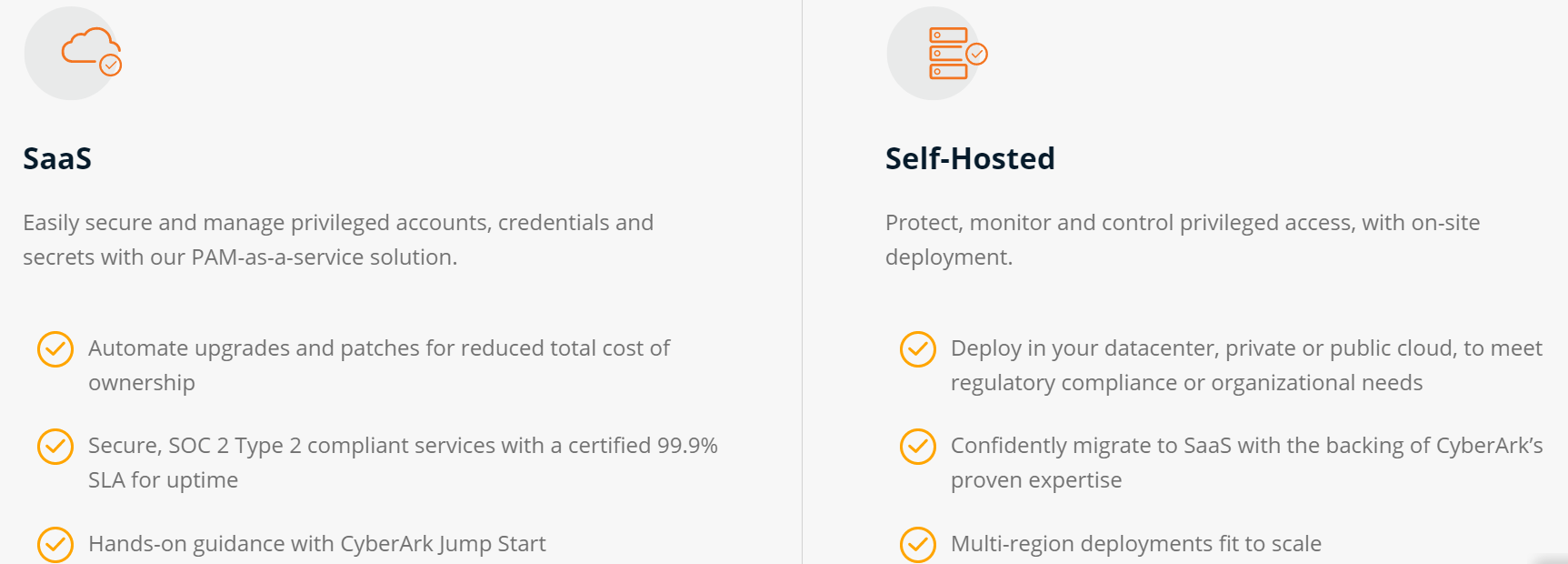
DEPLOY AS SAAS OR SELF-HOSTED
Implement and expand PAM with confidence. The CyberArk Identity Security Blueprint has successfully secured thousands of customer environments and counting.
Learn more: https://www.cyberark.com/products/privileged-access-manager/