LogRhythm UserXDR
24 Jul 2021User-based threats, such as compromised accounts and malicious insiders continue to increase risk and exposure across organizations, adding complexity to the already difficult challenge of defending against an evolving threat landscape. UserXDR, LogRhythm’s user entity behavioral analytics (UEBA) solution, automatically identifies and prioritizes anomalous user behavior, bringing enhanced visibility and efficiency to the detection of these malicious threats.
Quickly Find and Protect Against Known and Unknown Adversaries

Elevate threat hunting capabilities
Rapidly identify and investigate anomalous behavior to discover unknown threats

Increase detection accuracy of known threats
Reduce false positives through additional corroboration with user-based risk scores

Accelerate threat mitigation with embedded SOAR
Immediately respond to malicious activity with automated response actions
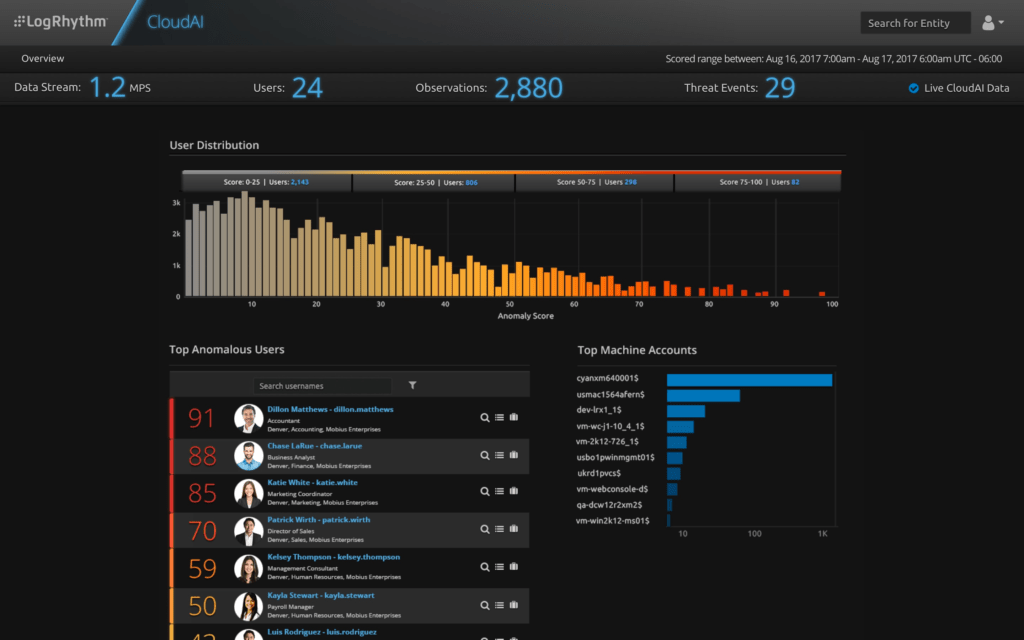
Gain Unique Insights From Behavioral Analysis Through Machine Learning
LogRhythm UserXDR deepens your knowledge using machine learning and analytics.
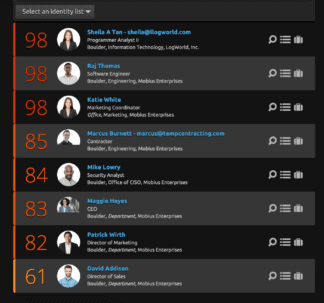
User-Based Risk Scores
Behavioral analysis establishes baselines and generates user scores that provide prioritization and evidence-based starting points to enhance investigations.
TrueIdentity™ User Attribution
Ensures accurate and collective analysis of all associated user activity by mapping disparate accounts and unique identifiers to build a singular user identity for comprehensive monitoring.
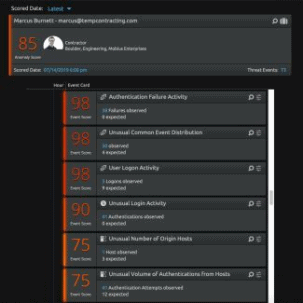
Event Timeline
Accelerate threat hunting and increase detection accuracy with user- and peer group-based contextual data that illustrates baseline deviation and threat progression.
Embedded SOAR
Built-in security orchestration, automation, and response (SOAR) capabilities accelerate detection and resolution of known and unknown user-based threats.
Solve the Most Common User-Based Threat Use Cases
Identify Malicious Insider Threats
Malicious insiders cause damaging, headline-making cyberbreaches and acts of sabotage. Monitor for data exfiltration, policy violations, and other dangerous activity.
Uncover Compromised Accounts
Attackers use compromised account credentials in an overwhelming number of breaches. Distinguish between legitimate account activity and compromised account activity through behavior profiling and anomaly detection. Discover the imposter before a damaging breach occurs.
Track Unauthorized Data Access and Exfiltration
When a compromised user account or a rogue insider finds sensitive data, you need to know. Our full-spectrum analytics and file integrity monitoring (FIM) can help you immediately detect when a user inappropriately accesses protected data.
Expose Privilege Abuse and Misuse
Your privileged users have the keys to the kingdom, presenting a greater risk to your organization. Track how users are applying these privileges by monitoring for unauthorized account creation, privilege escalation, abnormal access, and other risky activity.
Learn more: https://logrhythm.com/products/logrhythm-user-xdr/